The Advantages of Voice over IP (VoIP) Telephony
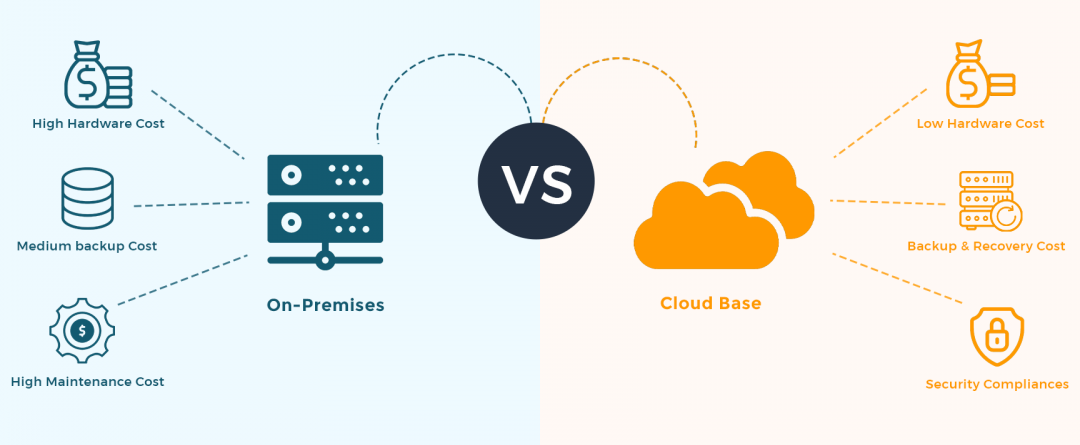
Businesses are constantly looking for ways to improve efficiency and reduce costs. One technology that has proven to be a game-changer is Voice Over IP (VoIP) telephony. This technology uses the internet to transmit voice data, transforming the way businesses communicate. Here are some key advantages of VoIP telephony: 1. Cost Savings One of the most significant advantages of Voice over IP is the potential for cost savings. Traditional phone services can be expensive, especially for long-distance and international calls. VoIP [...]