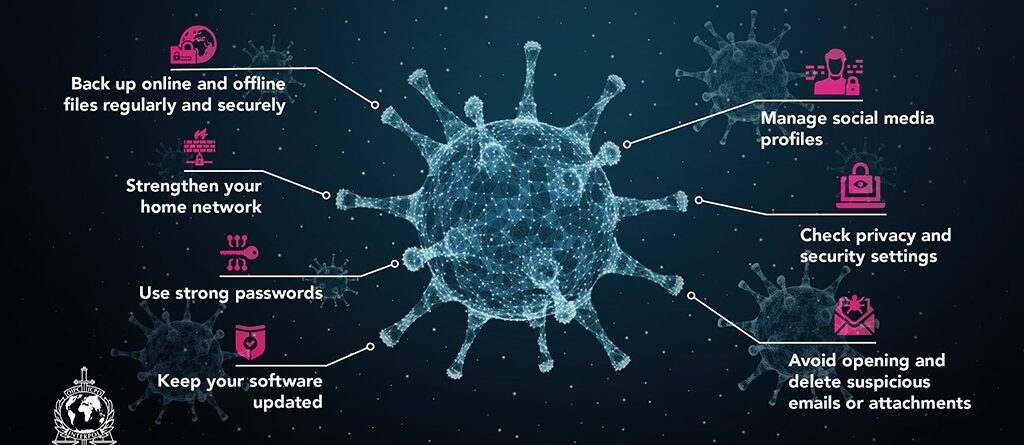
Data Encryption Strategies: Essential Tips
Data breaches can lead to severe financial losses and damage to reputation. Enter data encryption, a powerful security measure that shields information from unauthorized access. In this article, we will explore key tips for small businesses to create a robust data encryption strategy, enhancing data protection and ensuring compliance with privacy regulations. 1. Identify Critical Data Assets The first step in crafting an encryption strategy is identifying what data needs protection. Conduct a comprehensive inventory of your digital assets, classifying them [...]