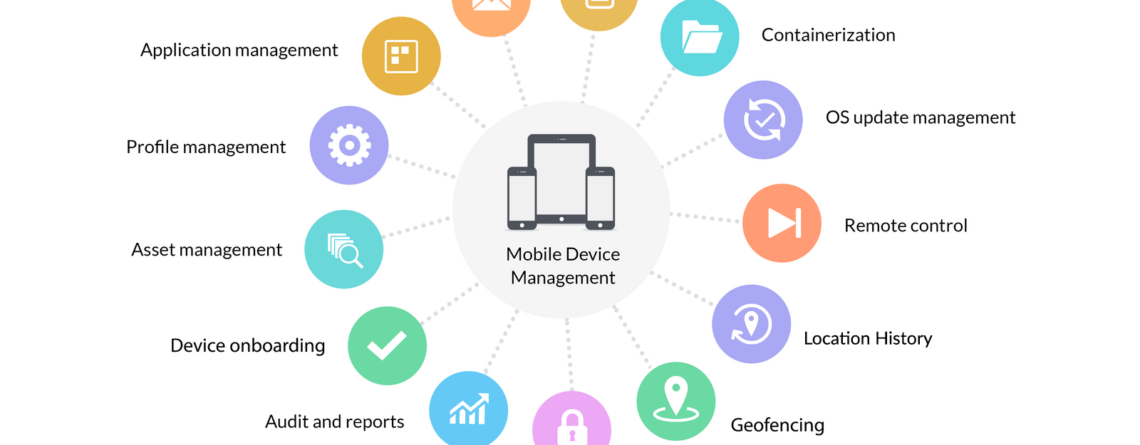
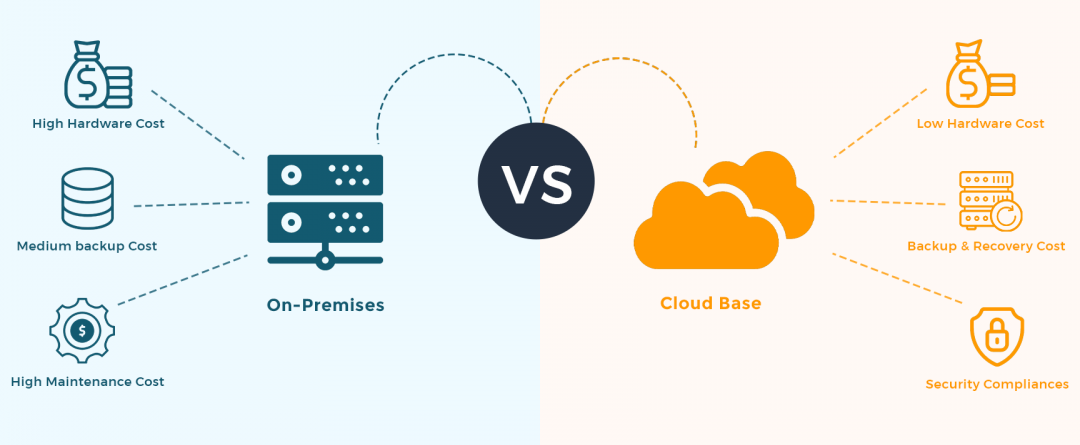
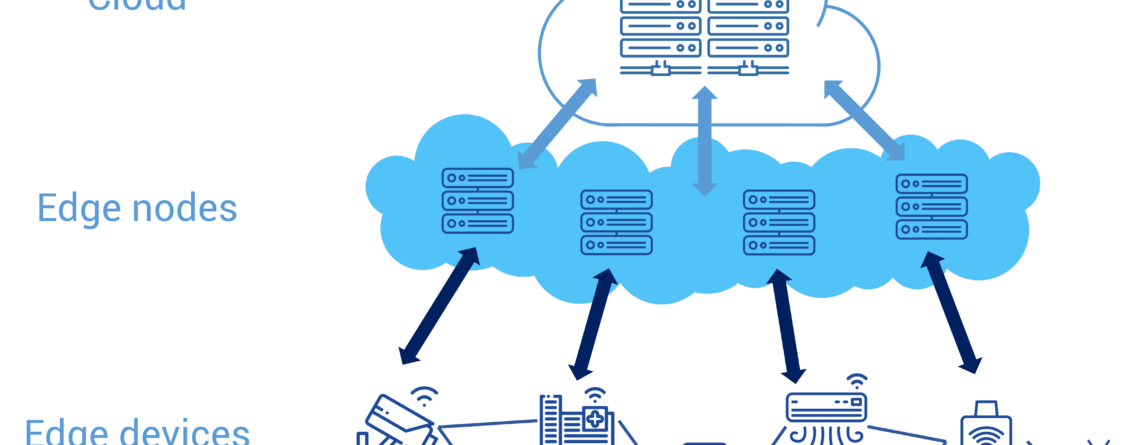
MDM: Tips for Implementing Mobile Device Management
In the ever-expanding realm of technology, managing mobile devices is a critical aspect of ensuring a secure and efficient work environment. Mobile Device Management (MDM) plays a pivotal role in maintaining control, security, and functionality across the diverse array of devices used in today's workplace. Here are a few actionable tips for implementing effective Mobile Device Management tailored to the needs of your business. Define Clear Mobile Device Policies Before delving into the technical aspects of MDM, it's essential to establish [...]