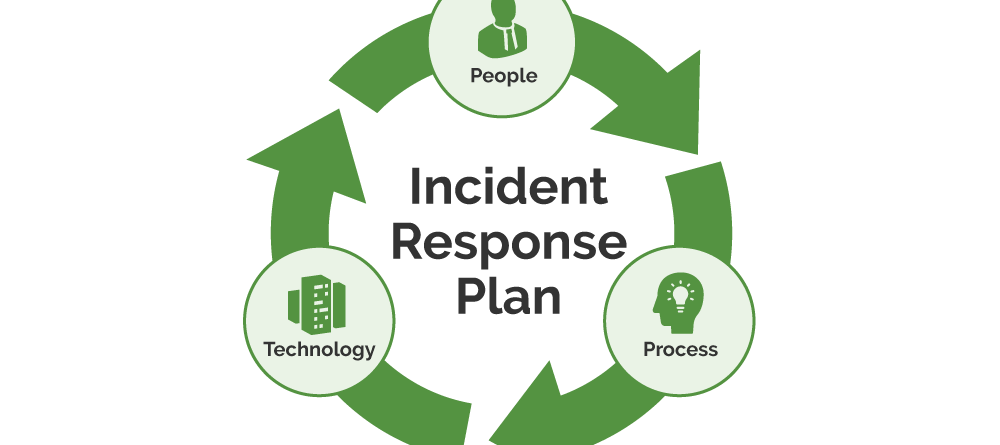
Building A Secure Remote Access Solution
The ability to work remotely is not just a luxury, but a necessity for many businesses. However, remote access can also pose significant security risks if not properly managed. Here are some tips for building a secure remote access solution. Understanding Remote Access Remote access allows employees to access company resources from any location. This can include accessing files, applications, and even controlling their office computer from home. While this flexibility can boost productivity and employee satisfaction, it also opens up [...]