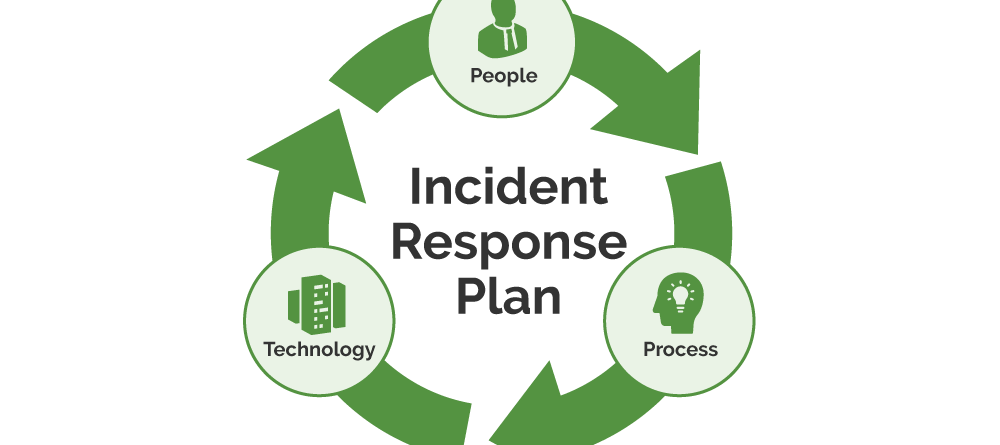
Creating an Effective Incident Response Plan
In the digital age, the security of your information is paramount. One crucial aspect of information security is an incident response plan. This guide will help you understand what an incident response plan is and why it's essential for your business. What is an Incident Response Plan? An incident response plan is a set of instructions that your IT team follows in the event of a security breach or cyber attack. It's like a fire drill for your data, ensuring that [...]